The hacker never entered his barn. Never touched a cow. But when ransomware encrypted his robot’s health data, a pregnant cow’s distress went invisible. She died. Cyber risk just hit the transition pen.

Executive Summary: A hacker never touched his cows—but a pregnant one died anyway. When ransomware encrypted a Swiss dairy farmer’s robotic milking system in 2024, the health data that could have flagged her distress went dark. By the time anyone noticed, she and her calf were gone. This is dairy’s new vulnerability: ransomware attacks on agriculture doubled in early 2025, now comprising 53% of cyber threats targeting the food industry. As digital tools increasingly drive fresh cow management, disease detection, and breeding decisions, cyber risk has become a transition pen issue—not just an IT problem. The encouraging news? Protecting your herd doesn’t require an IT department. Here’s a practical six-step framework, the questions to ask your technology partners, and what cooperatives and Congress are doing to help.

You know, a decade ago, the riskiest “system crash” on most dairies was a parlor vacuum pump going down right in the middle of milking. Today—and this has taken a lot of us by surprise—a growing number of those failure points live in software, routers, and cloud accounts.
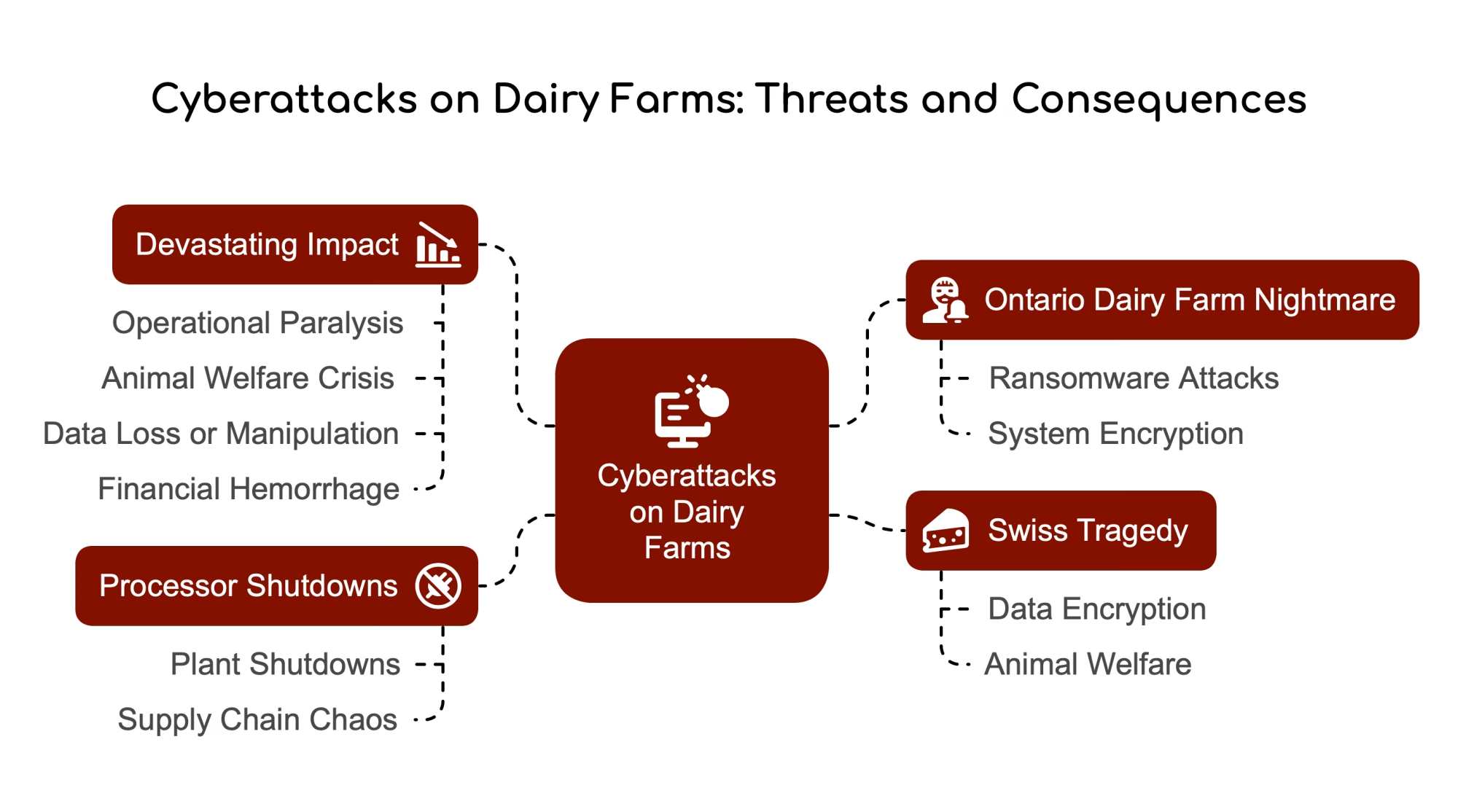
Here’s what brought this home for me. Back in 2024, a Swiss dairy farmer named Vital Bircher had his robotic milking system encrypted by hackers. They demanded about $10,000 in ransom. The physical robots kept milking—teat cups attaching, vacuums cycling normally—but he suddenly lost access to all the data that actually helps you manage cows. The health alerts, the conductivity readings, the reproduction flags. Without that information, a pregnant cow’s condition deteriorated before anyone caught it. Both she and her calf were lost. CSO Online and several European outlets covered the story, and it’s stuck with me ever since.

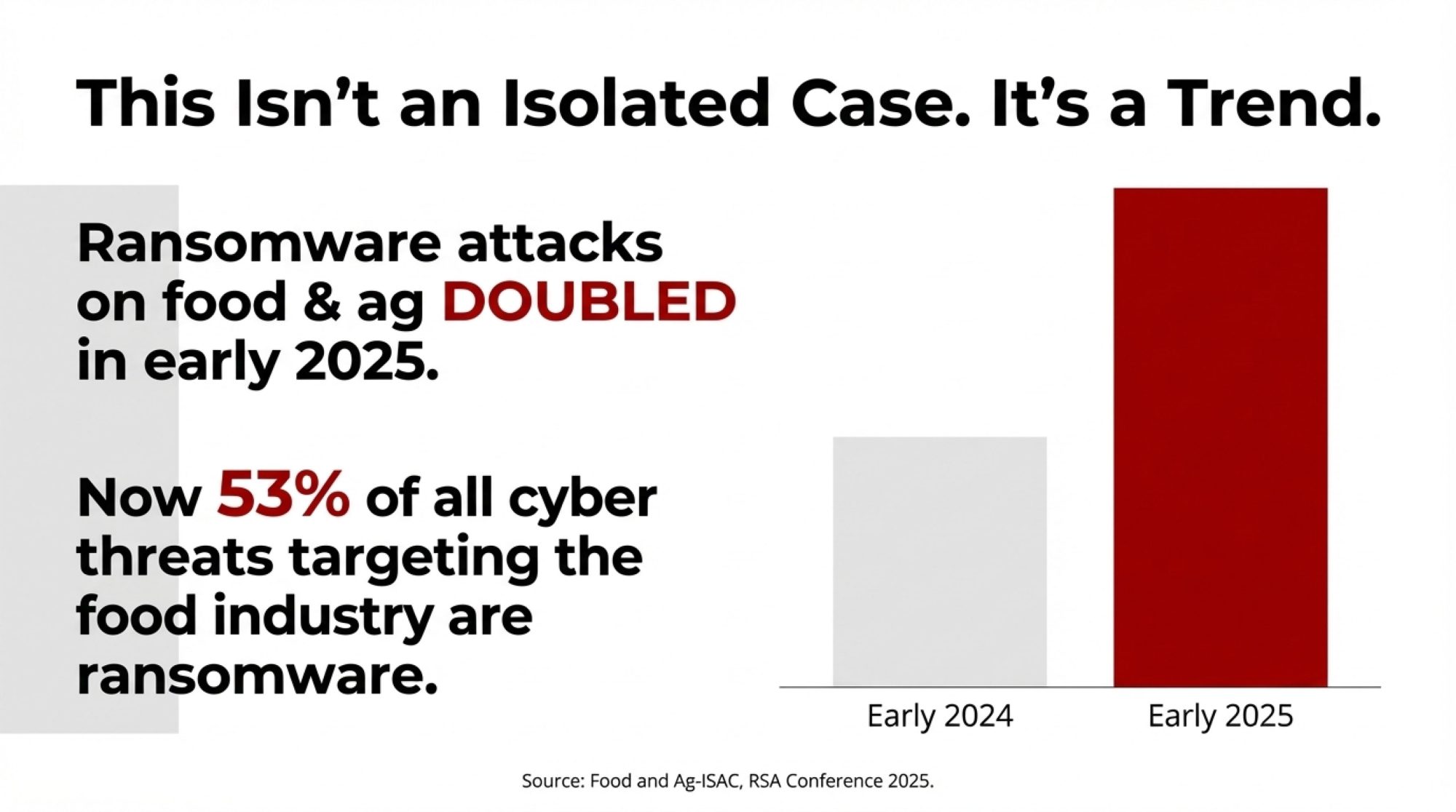
What’s sobering is that this isn’t an isolated incident. Jonathan Braley, director of the Food and Ag-ISAC, reported that ransomware attacks on food and agriculture more than doubled in early 2025 compared to the same period last year—84 incidents in just the first quarter. He presented those findings at the RSA Conference this past spring. Ransomware now accounts for roughly 53% of all cyber actors targeting the food industry.
So here’s what many of us are starting to realize: once your milking, feeding, and herd records move onto networks and into the cloud, dairy farm cybersecurity isn’t just “an IT problem” anymore. It becomes part of herd management, animal welfare, and business continuity.
The Digital Barn Is Already Here
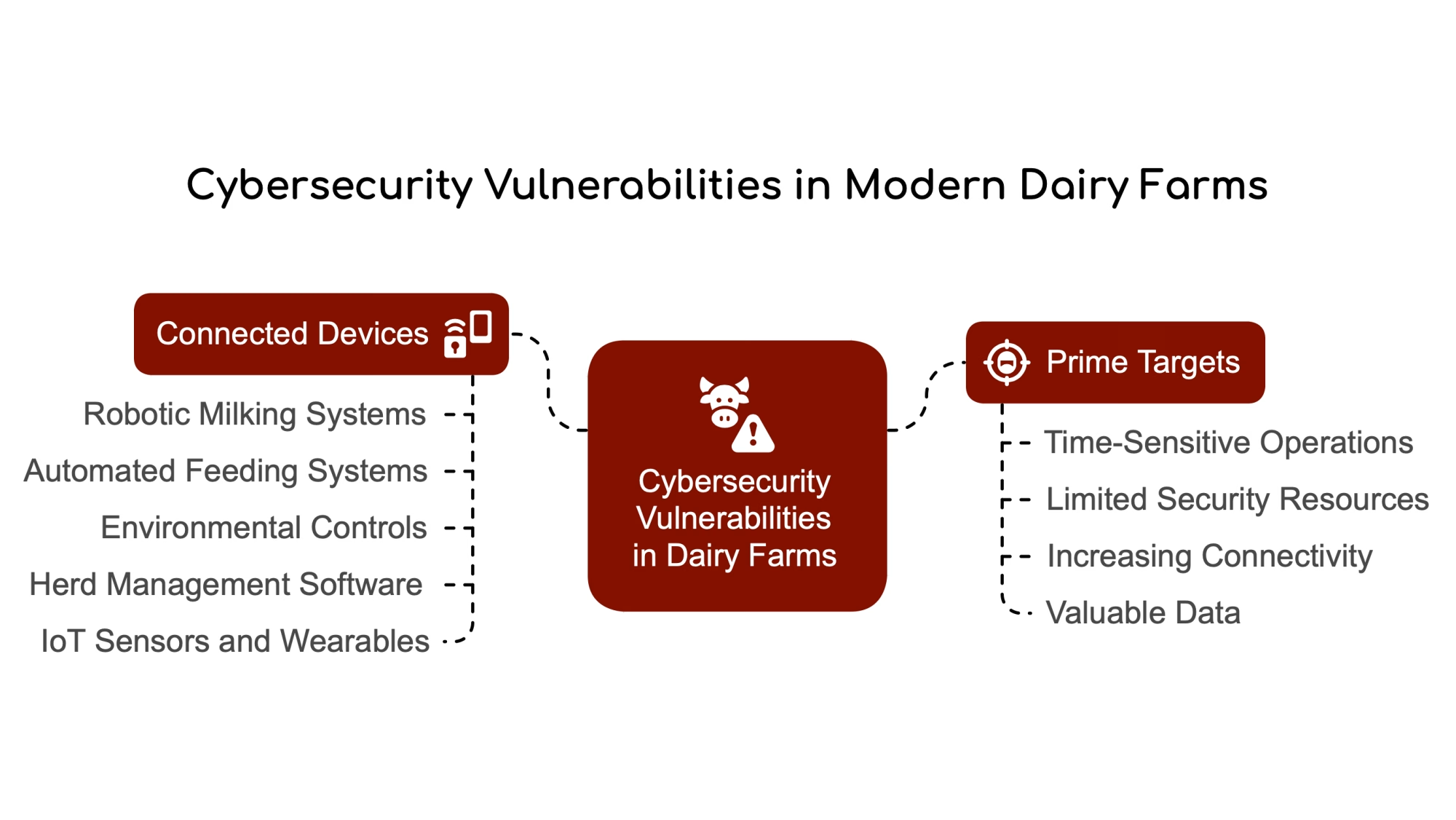
Walk into most progressive operations today—whether that’s a 200-cow freestall in Wisconsin, a large drylot in the Central Valley, a grazing operation in the Pacific Northwest, or a mega-dairy in the Texas Panhandle—and you’ll see it. Robotic milkers, activity collars, sort gates, in-parlor ID, and environmental controllers. At least one computer screen is glowing somewhere in the office. The digital dairy isn’t some future concept. It’s daily life.
A research team published a comprehensive roadmap earlier this year in Frontiers in Big Data—titled “Safeguarding Digital Livestock Farming”—and put dairy right at the center of this transformation. Sensors, automation, and AI are now embedded throughout milking, feeding, and health monitoring on commercial operations worldwide.
The benefits are real, and most of us have seen them firsthand. We’re catching mastitis earlier by monitoring milk conductivity. Activity and rumination data can flag fresh cow problems during that critical transition period—often 24 to 48 hours before you’d see clinical signs with your eyes. There’s solid research on this from Cornell and in journals like Nature Scientific Reports. Labor flexibility has improved with robots handling overnight milkings. Butterfat performance gets better when ration and intake data actually talk to each other.
But here’s the flip side that same Frontiers paper points out: as these systems have come online, the “attack surfaces” have multiplied. Vulnerabilities in barn controllers, herd software, and cloud services can now impact animal care and milk flow as surely as a broken pipeline once did.
The technology and threat curves are rising together. That’s simply the reality we’re operating in now.
When a Cyberattack Actually Reaches the Cows

Let me walk through what happened in Switzerland, because it illustrates how digital problems connect to cow comfort in a very concrete way.
When hackers encrypted Vital Bircher’s robotic milking system, the physical equipment kept running. Teat cups still attached. Vacuums still cycled. But suddenly, he couldn’t see quarter-level milk yield and conductivity, changes in milking duration and flow rate, temperature and milk quality indicators, or health and reproduction flags tied to individual cows.
If you’ve worked with robotic systems—whether Lely, DeLaval, GEA, or others—you know how much you come to rely on that information for daily management decisions. Several controlled studies have shown that milk conductivity, yield deviations, and rumination data can flag subclinical mastitis, ketosis, and other issues a day or two before a cow shows obvious clinical signs. In a fresh cow management context, that head start matters enormously.
What’s worth noting here is that, in Bircher’s case, the cows, the feed, and the barn didn’t change fundamentally. What changed was his ability to see trouble coming. Once that data stream stopped, the margin for error around sick cows and high-value pregnancies narrowed fast.
He didn’t pay the ransom. But his total losses—vet costs, a new computer, the animals—ran around 6,000 Swiss francs. More than the money, though, it shook his confidence in systems he’d built his operation around.
“When you’ve structured your fresh cow protocols around digital data, losing access to that data isn’t just inconvenient—it fundamentally changes how you can care for your animals.”
That’s the part that resonates with a lot of producers. When you’ve built your health monitoring and fresh cow management around digital data, losing access isn’t a minor setback. It changes your entire approach to animal care.
Who’s Actually Paying Attention to Agriculture?
It’s fair to ask: “Am I really on anybody’s radar with 200 cows in a freestall?” The evidence suggests the answer is yes—though the motivations vary quite a bit.

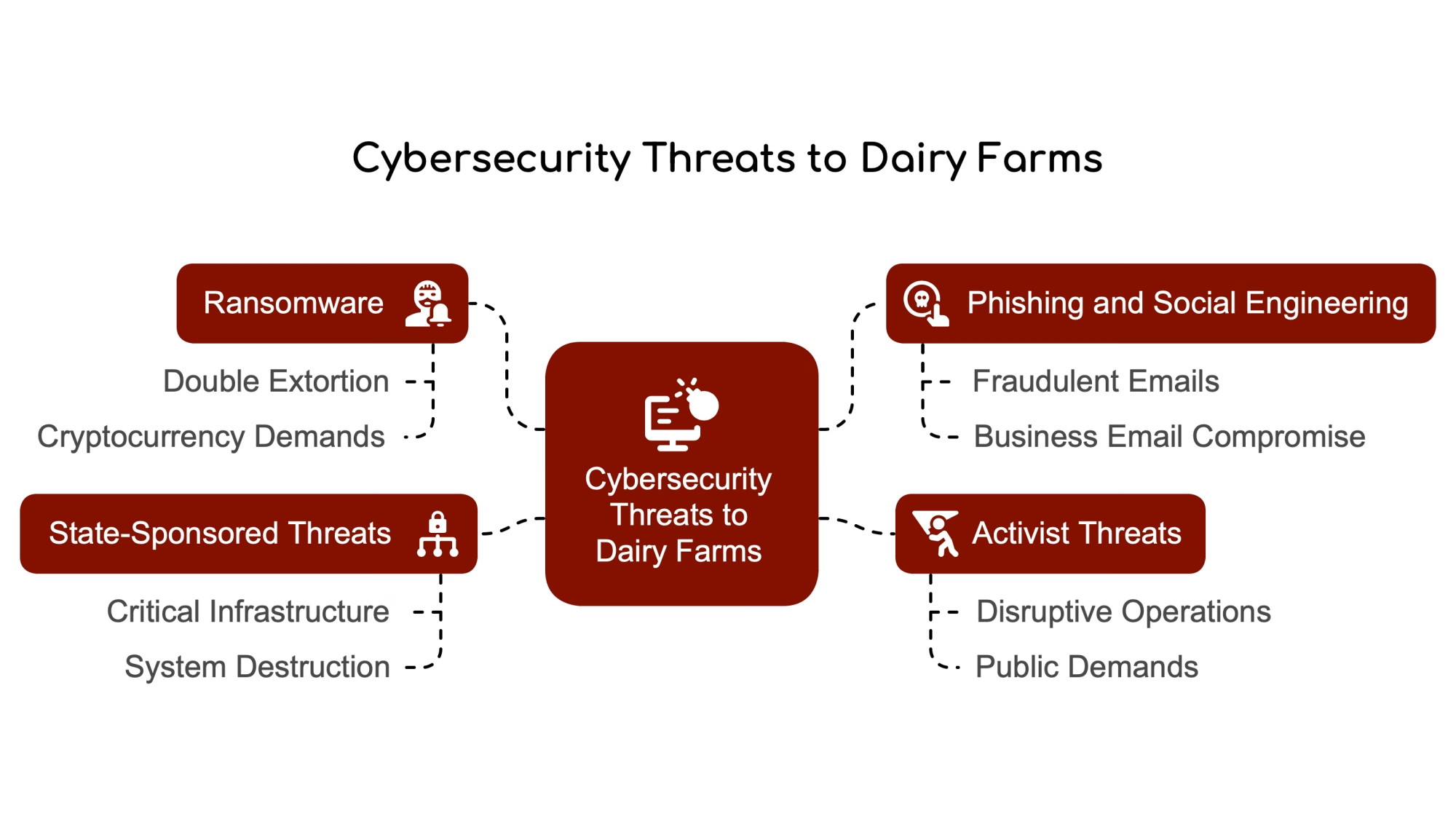
Ransomware operators have definitely noticed agriculture. In 2021, the FBI, CISA, and NSA issued a joint advisory warning that ransomware groups were targeting the food and agriculture sectors. They’d hit two U.S. food and ag organizations with BlackMatter ransomware. Then, in April 2022, the FBI issued another bulletin warning that attackers might time their hits to planting and harvest seasons—when downtime hurts most, and there’s pressure to pay quickly. Brownfield Ag News reported that at least seven grain cooperatives had already suffered ransomware attacks in the fall of 2021.
Since then, we’ve seen plenty of real-world examples. In June 2025, multiple Dairy Farmers of America manufacturing plants got hit with ransomware. The Play ransomware gang later claimed responsibility, and according to reporting in The Record, data from over 4,500 individuals was compromised. DFA worked through recovery—and credit to them for being relatively transparent about what happened—but it showed how a single upstream compromise can ripple through plants, routes, and eventually farm milk checks.
| Incident | Category | Cost/Impact |
|---|---|---|
| Swiss Farmer (Vital Bircher) | Ransom Demanded (unpaid) | $10,000 |
| Swiss Farmer (Vital Bircher) | Veterinary Costs | $2,304 |
| Swiss Farmer (Vital Bircher) | New Computer | $1,000 |
| Swiss Farmer (Vital Bircher) | Lost Animals (cow + calf) | $2,696 |
| Swiss Farmer (Vital Bircher) | TOTAL OUT-OF-POCKET | $6,000 |
| DFA Cooperative Attack | Plants Disrupted | Multiple facilities |
| DFA Cooperative Attack | Individuals Compromised | 4,546 people |
| DFA Cooperative Attack | Payment Processing Delays | 17 days |
| DFA Cooperative Attack | Estimated Revenue Impact | Systemic – milk checks delayed |
Nation-state actors appear to be playing a longer game. This is the part that can feel a bit surreal to discuss at a farm level, but cybersecurity analysts increasingly point out that countries like China, Russia, and North Korea view food and agriculture as strategic infrastructure. A Forbes analysis last fall by Daphne Ewing-Chow noted that the FBI identifies four major threats to agriculture: ransomware attacks, foreign malware, theft of data and intellectual property, and bio-terrorism. FBI Special Agent Gene Kowel was quoted as saying that “foreign entities are actively seeking to destabilize the U.S. agricultural industry.”
For dairy, that could mean interest in genomic data, feeding strategies tied to high components, or disease management approaches. The goal isn’t a quick ransom—it’s gaining competitive advantage by shortcutting years of R&D. From our perspective on the farm, this kind of data theft can be nearly invisible. Whether it’s a significant risk for individual operations or primarily affects larger genetics companies and cooperatives is still being understood.
There’s also an emerging activist angle. Dr. Ali Dehghantanha—he holds the Canada Research Chair in Cybersecurity and Threat Intelligence at the University of Guelph—has been tracking a newer trend. His lab worked on a case involving an Ontario hog operation that was hit with ransomware, but the attackers didn’t want money. They wanted a public confession of animal cruelty. The Western Producer covered the story earlier this year.
As Dr. Dehghantanha put it, “As activists educate themselves on cyberattack techniques, they are becoming a significant, emerging risk in agriculture.” It’s a different motivation than the ransomware gangs, but it’s part of the picture worth being aware of.
Where the Practical Vulnerabilities Are
Most of us don’t have time to become network engineers. So let me walk through the concrete weak spots that keep showing up in farm-focused cybersecurity assessments. These are things you can actually check on your own operation.

Factory-default passwords remain surprisingly common. You know how your router probably came with “admin/admin” as the login? A lot of barn cameras, remote-access modules, and some equipment controllers ship the same way. Those defaults are published in manuals and all over the internet. If nobody ever changes them, automated scanning tools can find and access those devices pretty quickly.
Security assessments consistently identify unchanged default credentials as one of the most common vulnerabilities on farm systems. It’s understandable—we’re focused on the cows, not the router password—but it’s also one of the easiest openings to close.
Everything often runs on one network. On many operations—I’ve seen this pattern from Wisconsin tiestalls to California drylots to Northeast grazing dairies—the setup looks like this: one router from the ISP, a few switches, and everything plugged in together. Robots, office computers, herd software, phones, cameras, tablets. All on the same network.
Security professionals call this “flat networking,” and they consistently flag it as a significant risk. Here’s why it matters: once an attacker gets into any device—say, a poorly protected camera—they can potentially move sideways to more critical systems. Your herd management server. Your robot controls. Your financials.
Firmware updates often get skipped. Just like your phone receives updates, so do routers, controllers, and automation components. Those updates frequently contain security fixes. But on farms, updating firmware often requires a technician visit or carries the risk of breaking something that’s working fine. So a lot of equipment runs older, vulnerable software versions long after fixes are available.
Single passwords often protect critical accounts. Most herd management and financial portals now support multi-factor authentication—that extra code sent to your phone. But as both Hoard’s Dairyman and Dairy Herd Managementhave noted, plenty of producers still rely on just a password. Given how many password databases have been breached over the years, that’s a real exposure worth addressing.

| Defense Step | Cost | Time Investment | Impact Level | Protects Against |
|---|---|---|---|---|
| 1. Change Default Passwords | $0 | 1 hour | HIGH | Automated scans, default exploits |
| 2. Enable Multi-Factor Authentication | $0 | 2 hours | HIGH | Stolen password attacks |
| 3. Create Offline Backup System | $100-150 | 4 hours setup + monthly backups | CRITICAL | Complete data loss, ransom pressure |
| 4. Segment Your Networks | $500-2,000 | 1 day + IT consultant | HIGH | Lateral movement after breach |
| 5. Train Your Team | $0-500 | 2-4 hours annually | MEDIUM-HIGH | Phishing, social engineering |
| 6. Document Incident Response Plan | $0 | 4 hours | CRITICAL | Chaos during active attack |
What’s Actually Working: A Practical Framework
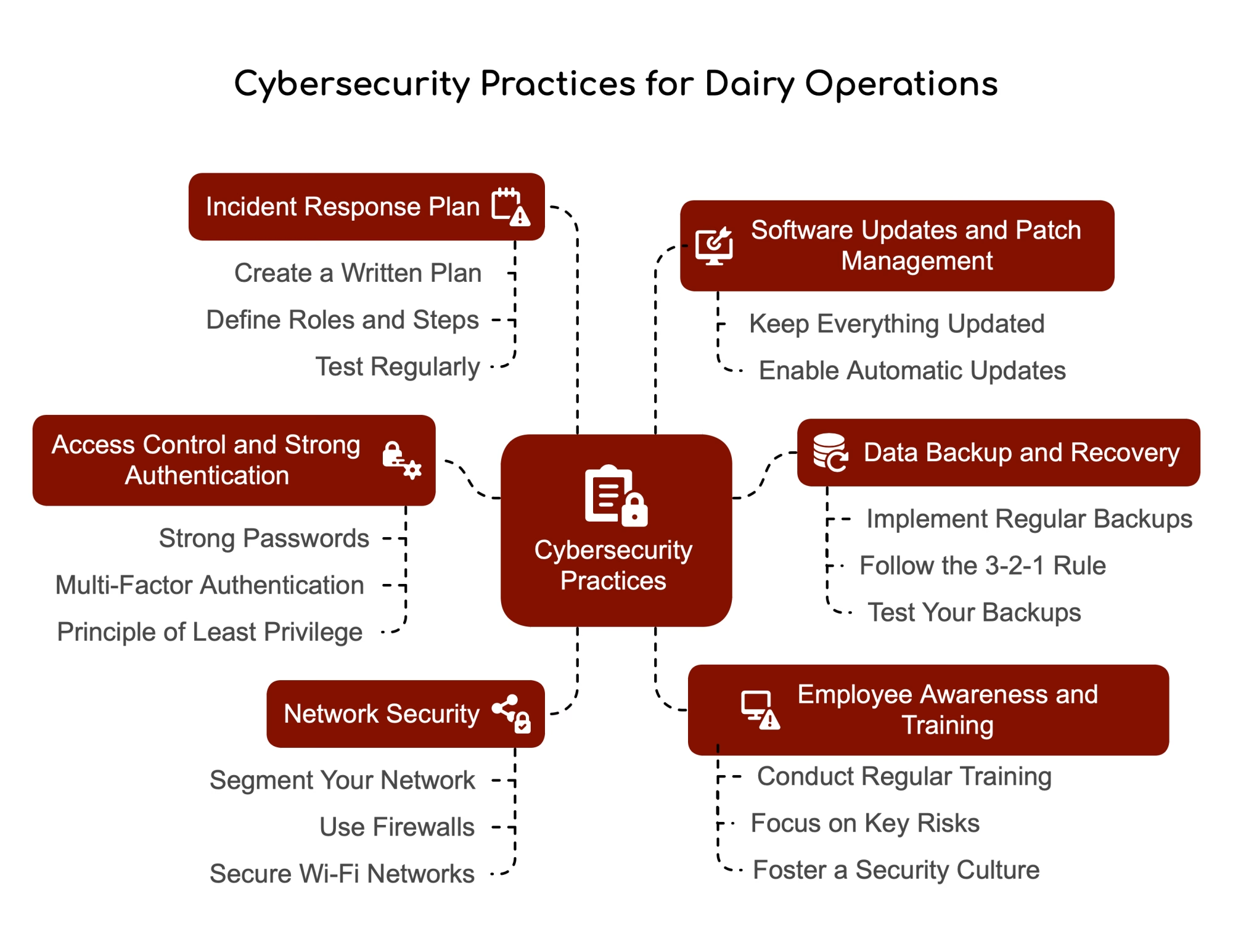
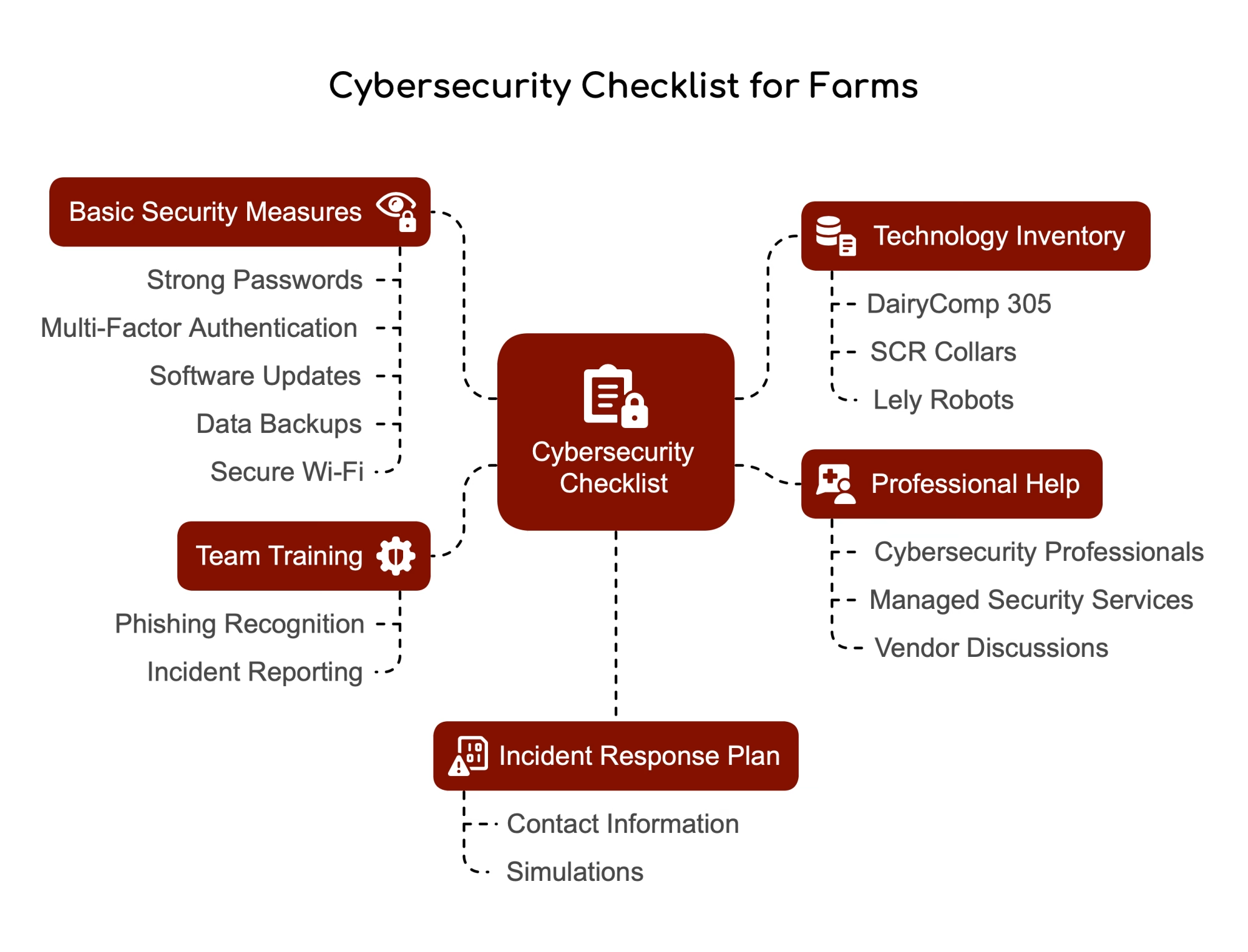
The encouraging news—and there is encouraging news here—is that you don’t need an IT department to improve your farm data security meaningfully. Extension work in Canada, federal guidance from CISA, and sector-specific research all point to a straightforward staged approach that makes a real difference.
Start by taking inventory of your digital barn. This sounds basic, but it matters. Walk the farm and list everything that’s connected to it. Robots, feed systems, herd management computers, environmental controllers, cameras, office machines, and cloud accounts for herd data or milk marketing. For each one, note what it does, who uses it, and whether it touches herd data, financials, or insurance information.
It’s a bit like walking pens for fresh cow checks—you can’t manage what you don’t know is there.
Then close the obvious doors. Several defenses cost little or nothing. Change those default passwords on your router, cameras, and remote-access logins. Use strong, unique passwords—and if a password manager feels like overkill, a written log kept in a locked filing cabinet works fine. It’s far better than using the same password everywhere.
Turn on multi-factor authentication wherever you can. Cloud herd software, email, banking—they almost all support it now. It adds a small step to logging in, but it makes stolen passwords significantly less useful to attackers.
Here’s something simple that security professionals recommend: restart your phones and tablets regularly. It helps get updates applied and clears temporary data where some malware operates. Not a bad habit to pair with morning coffee.

Make sure you can recover offline. When ransomware hits, one of the first things it typically does is look for and encrypt any backups it can reach. That’s why Agriculture and Agri-Food Canada’s cyber security toolkit and programs like CSKA—the Cyber Security Knowledge Alliance—recommend having at least one offline backup. A copy of key data that’s physically disconnected from the network most of the time.
On a 200-cow dairy, a practical routine might look like this: buy an external hard drive—good options run $100 to $150. Once a month, connect it to a trusted office computer and copy critical data, including herd records, breeding and genomic information, ration files, and accounting records. Then disconnect it and store it in a safe, dry place.
If the worst happens, you might lose a few weeks of recent notes. But you won’t lose years of herd history or your entire genetic program.
Consider segmenting your networks. This is where a local IT consultant can really help, but the concept is straightforward. Instead of running everything through one router, you split traffic into separate lanes:
- Operations network: milking system, feeding controls, environmental controllers
- Office network: business computers, maybe a dedicated herd management PC
- Guest network: phones, visitor WiFi, cameras, and less critical devices
Modern small-business routers from companies like Ubiquiti or Cisco can create separate virtual networks, with rules specifying which devices can talk to which. Devices on the guest network can reach the internet, but can’t communicate with your robot controller.
What this accomplishes is similar to what a good pen layout does: it limits how far a problem can spread. If a phone or camera gets compromised, that doesn’t automatically provide a path to your herd management server.

Bring your team into the conversation. Cyber awareness training doesn’t have to mean long courses. Dr. Dehghantanha’s work at Guelph and several farm-focused consulting groups have found that a short, plain-language briefing makes a meaningful difference.
Cover phishing—show examples of suspicious emails that pretend to be from a bank, supplier, or milk buyer asking for login credentials. The key message: don’t click links in unexpected emails. Go directly to the site you already know, or pick up the phone and call. Discuss password practices—no sharing, no sticky notes on the robot room computer. And make sure everyone understands: if something looks weird, say something. Many breaches escalate simply because nobody wanted to raise a concern.
Have a basic plan for when something goes wrong. Just like every farm has a plan for a parlor breakdown or power outage, it’s worth writing down a one-page playbook for suspected cyber incidents. Who gets called first—IT support, equipment dealer, co-op field rep, insurance agent, maybe a law enforcement contact. How to isolate an affected system without shutting down equipment in ways that could harm animals. Where the offline backups are stored and who can authorize a restore.
Think of it like a herd health protocol—you may refine it over time, but having something written down keeps everyone from improvising during a stressful situation.
| System Category | Device/System | Data at Risk | Default Password Risk |
|---|---|---|---|
| Milking Systems | Robotic milking units | Cow IDs, milking schedules, yield data | HIGH |
| Milking Systems | Parlor identification systems | Individual cow tracking, timestamps | HIGH |
| Milking Systems | Milk meters & sensors | Production metrics, quality alerts | MEDIUM |
| Milking Systems | Conductivity monitors | Mastitis detection, SCC levels | MEDIUM |
| Herd Health Monitoring | Activity/rumination collars | Behavior patterns, health alerts | MEDIUM |
| Herd Health Monitoring | Health monitoring software | Treatment records, disease history | LOW |
| Herd Health Monitoring | Breeding/reproduction platforms | Heat detection, pregnancy status, insemination dates | LOW |
| Herd Health Monitoring | Genomic data systems | Genetic profiles, breeding values | LOW |
| Barn Automation | Automated feeders | Ration formulas, intake patterns | HIGH |
| Barn Automation | Environmental controllers | Temperature, humidity, barn conditions | HIGH |
| Barn Automation | Sort gates & cow traffic | Pen assignments, movement logs | MEDIUM |
| Barn Automation | Ventilation systems | Air quality, fan controls | HIGH |
| Business Systems | Office computers | Financial records, employee data | LOW |
| Business Systems | Cloud herd management | Complete herd history, performance analytics | LOW |
| Business Systems | Financial/banking portals | Bank accounts, payment information | LOW |
| Business Systems | Milk marketing platforms | Milk prices, shipment schedules | LOW |
| Network Infrastructure | WiFi routers | Network access, device passwords | CRITICAL |
| Network Infrastructure | Security cameras | Video footage, facility surveillance | CRITICAL |
| Network Infrastructure | Remote access modules | VPN credentials, remote login | CRITICAL |
| Network Infrastructure | Mobile devices/tablets | Email, app passwords, two-factor codes | MEDIUM |
Questions Worth Bringing to Your Vendors and Co-ops
One positive shift I’ve noticed recently is that producers are no longer simply assuming their technology partners have security covered. More farmers are asking direct—but fair—questions of dealers, software providers, and cooperatives.
For equipment dealers and OEMs, questions like these are reasonable to ask:
- How are passwords and remote access handled on this system? Can factory defaults be changed easily?
- Does communication between controllers and robots use encryption, or does it travel as plain text on the network?
- How often do you release security updates, and what’s the process for applying them?
- If a vulnerability is discovered, how will you notify customers?
For herd management and cloud software providers:
- Where is my herd data physically stored—what country, what type of data center—and how is it protected?
- Is multi-factor authentication available for my account?
- Do you have a documented incident response plan? Will I be notified if my data is accessed inappropriately?
For co-ops, processors, and lenders:
- Do you offer cybersecurity programs or shared services that member farms can access?
- Are there minimum security practices you expect from suppliers?
- Is cyber coverage available as part of broader farm risk insurance, and what does it require?
These aren’t adversarial questions. They’re the same kind of due diligence we already practice around milk quality testing, residue protocols, or animal care standards. Vendors who take security seriously generally welcome the conversation.
How the Broader Industry Is Responding
To be fair, the industry hasn’t been asleep at the wheel here. Several encouraging developments are worth knowing about.
That Frontiers in Big Data roadmap I mentioned earlier was developed by academic, industry, and policy experts specifically to give dairy and poultry clearer guidance on security. Organizations like the Food and Ag-ISAC have grown substantially to help producers and processors share threat information.
What’s particularly interesting is what rural electric cooperatives have accomplished. Through NRECA’s Rural Cooperative Cybersecurity Capabilities program—known as RC3—more than 500 co-ops have built stronger cybersecurity programs by pooling resources. Training, monitoring, and incident response—capabilities no single small utility could afford alone.
Several dairy and crop cooperatives are now studying that model. What might it look like applied to our sector? A regional cooperative could potentially offer shared threat monitoring, collective incident response capabilities, vendor vetting, and centralized training for member farms. Cost might run $50 to $100 per month through the milk check—but the benefit would be access to security resources that no individual 200-cow operation could afford on its own.
On the policy front, Congress introduced the Farm and Food Cybersecurity Act in February 2025, in both the House and the Senate. The legislation aims to give USDA and CISA clearer authority and funding to develop sector-specific guidance. Whether it passes with meaningful resources remains to be seen, but it signals that agriculture has finally gotten the attention of federal cybersecurity agencies.
Bringing It All Together
Looking at everything we’ve covered, the core lessons for most dairy operations come down to a few practical points.
Your digital systems have become as operationally critical as your physical infrastructure. Robotic milkers, activity collars, and herd software are already shaping daily decisions around fresh cow protocols, reproduction timing, and treatment interventions. Protecting those systems is part of protecting the herd.
Most attackers look for easy targets, not sophisticated defenses. The majority of successful attacks in agriculture still exploit basic gaps—default passwords, missing multi-factor authentication, flat networks, and inadequate backups. Addressing those fundamentals won’t make any operation bulletproof, but it creates meaningful separation from operations that haven’t done the work.

A practical dairy farm cybersecurity program can be built through consistent habits rather than massive investments. Know what’s connected on your operation. Improve your password practices and enable MFA where available. Maintain at least one offline backup. Separate barn systems from guest WiFi if feasible. Give your team basic awareness training. Document a simple incident response plan.
None of this requires becoming a full-time IT specialist. It’s the same disciplined approach we already bring to biosecurity protocols or fresh cow management: identify vulnerabilities, apply reasonable controls, review periodically, and work with trusted partners where it makes sense.
What this suggests is that as dairy continues to embrace digital tools for component performance, labor efficiency, and animal care, cyber hygiene will quietly join feed cost management, reproductive programs, and milk quality as one of the background disciplines that distinguish resilient operations from fragile ones.
It’s one more responsibility on an already full plate. But it’s also one of the few areas where a modest investment of time can protect years of breeding progress, operational data, and hard-earned equity.
On today’s digital dairies, that’s work worth prioritizing.
KEY TAKEAWAYS
- Attacks doubled in 2025: Ransomware incidents in food and agriculture more than doubled this year. 53% of cyber actors targeting the industry now use ransomware
- Cyber risk hit the transition pen: When hackers encrypted a Swiss farmer’s robot data, health alerts went dark. A pregnant cow’s distress went unseen—she and her calf were lost
- Attackers exploit basics, not sophistication: Default passwords, flat networks, and missing backups are the doors they walk through. These gaps are fixable
- Protection costs less than you think: An external drive runs $100-150. Multi-factor authentication is free. Network segmentation pays for itself in risk reduction
- Three steps to start this week: Change default passwords on routers and cameras. Enable MFA on herd software and banking. Create your first offline backup
Complete references and supporting documentation are available upon request by contacting the editorial team at editor@thebullvine.com.
Learn More:
- The Tech Reality Check: Why Smart Dairy Operations Are Winning While Others Struggle – Essential reading for producers installing new systems. This guide reveals the “hidden costs” of technology adoption and provides a specific readiness checklist—including critical cybersecurity protocols like network segmentation—to ensure your investment delivers ROI rather than risk.
- Decide or Decline: 2025 and the Future of Mid-Size Dairies – Strategies for the 200-500 cow herd manager. This analysis demonstrates how “doing nothing” drains equity and provides a financial roadmap for mid-size operations to survive consolidation by treating data and planning as core business assets.
- Revolutionizing Dairy Farming: How AI, Robotics, and Blockchain Are Shaping the Future – Understand exactly what you are protecting. This article details the specific value of AI-driven health data—from mastitis prediction to genetic markers—illustrating why losing access to this “digital gold” is more costly than the ransom itself.
 The Sunday Read Dairy Professionals Don’t Skip.
The Sunday Read Dairy Professionals Don’t Skip.
Every week, thousands of producers, breeders, and industry insiders open Bullvine Weekly for genetics insights, market shifts, and profit strategies they won’t find anywhere else. One email. Five minutes. Smarter decisions all week.






 The Sunday Read Dairy Professionals Don’t Skip.
The Sunday Read Dairy Professionals Don’t Skip.